In a plugged-in world, centered around social media, the news, and everything online, cybersecurity is of utmost importance now more than ever before.
Protecting yourself from hackers, phreaks, and cybercriminals with malicious intent can be rather difficult nowadays, but it is extremely important for your online safety.
Today, malware and other forms of attacks on personal computers run rampant throughout the entire Internet, so it is essential to know what to look out for and take preventative measures against malware and hackers trying to steal your precious personal information and use it for evil purposes, like selling your data.
Here are a few ways you can avoid scammers online, as well as some information on what to look out for when actively avoiding scammers.

1. Do Your Research
Hackers employ a technique called social engineering, which is the term used to describe how hackers manipulate victims into performing certain actions or giving out confidential personal details. Social engineering is psychological and plays with the minds of its victims.
Phishing
One of the most well-known and common ways hackers dishonestly acquire your personal information is through phishing. Phishing, according to phishing.org, comes from an early term used for a type of hacker, known as a phreak. Phreaks study telecommunication systems as a means to use social engineering to psychologically manipulate people.
Phishing is the act of artificially creating a sense of urgency or curiosity in victims through emails or text message campaigns. For example, phishing could reach you in the form of an email that describes a policy change of a service you use, like a bank, and it creates urgency by claiming to require immediate action.

The phishy email may include a link, which, if you’re smart, you won’t click on. But, if you do, it will lead you to a site that appears to be the regular website you use, when in fact it is quite illegitimate. Because the email created a sense of urgency, you’ll quickly enter your credentials, and that means the hacker has successfully received your personal information and can use it to steal your money and even possibly your identity.
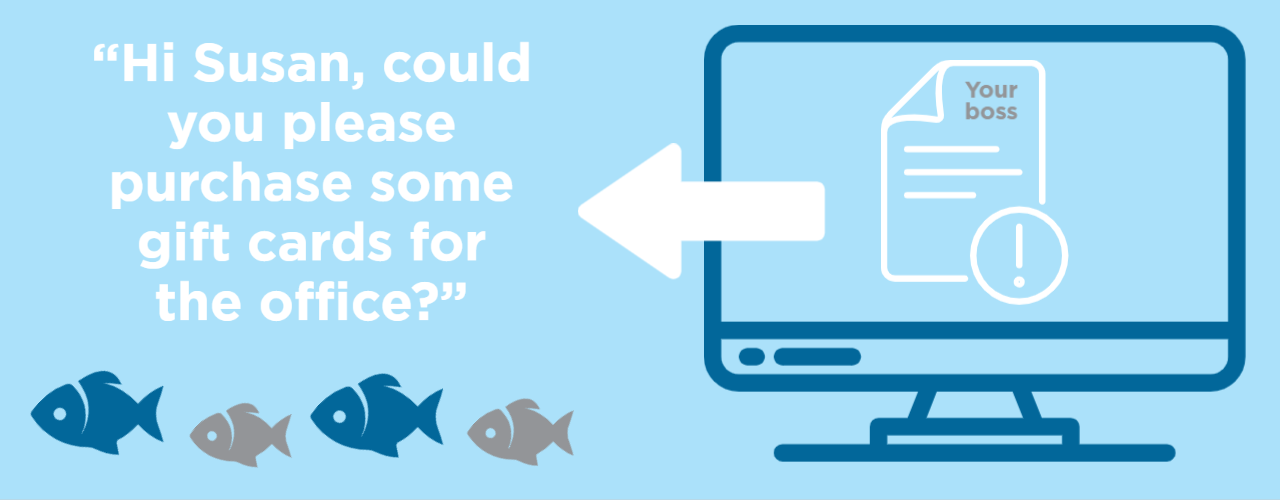
Spear Phishing
There are also more specific types of phishing, such as spear phishing, which aims directly at a specific person, instead of using a campaign that sends the same message to a large group of people.
Typically, spear phishing involves impersonating a member of the victim’s organization, like a boss or IT consultant. It’s worded in a way that imitates the boss, which can deceive the victim into thinking the message is real. The victim then gives up personal information, thinking they are giving it to a trusted individual, and then the spear phishing has been executed successfully.
Other Types of Phishing
Other types of phishing include whaling, smishing, and vishing, and all use social engineering to cause a person to give up personal details. Make sure you stay aware and alert of all these types of ploys to avoid falling for a scam and risking having personal details stolen from you. Once personal data has been given, it becomes easy for a hacker to place malware on your computer or even sell your data to even worse cybercriminals.

2. Stay Cautious
To prevent malicious attacks, it is much better to be safe than sorry. For example, if you have reason to believe a spear phishing email has been sent to you, you should approach the person that the hacker impersonated and check if that person sent you a message.
It is in your best interest to risk mild embarrassment rather than loss of money or personal details. Remain cautious of links provided in emails, and do not click them, as that action alone can cause malware to be installed on your computer.

3. Protect Your Passwords
There are many steps you can take to better protect yourself against cybercriminals, and most actions are pretty simple. One of the best ways to make sure your passwords don’t get compromised is to simply memorize them, instead of saving them to Google or another password manager.
Even if you have a lot of passwords, memorization is simple and will benefit you and protect you better online. Even physically writing them down and then storing them in a safe place is better than keeping them linked to your Google account. It is best to put as little personal information on the Internet as possible.
Simple Do's & Don'ts
- Do use complicated passwords so that they are harder to guess.
- Don’t use the same password for multiple accounts.
- Do make sure your content is backed up securely.
- Don’t share your passwords with other people.
- Do enable multi-factor authentication to help keep your information as secure as it can be.
- Don’t access banking or any other sensitive accounts through public Wi-Fi, as that is an easy way for hackers to gain access to your computer or phone.
It’s fairly easy to take steps toward protecting your data. If you are actively taking preventative measures against potential cybercriminals, you can rest a bit easier.

